Home » Uber has been HACKED By a Teen

Uber says it’s investigating a “cybersecurity incident” and alerted the law-enforcement authorities. The alleged hacker, who claims to be an 18-year-old, says they have administrator access to company tools including Amazon Web Services and Google Cloud Platform. The New York Times reports that the ride-hailing business has taken multiple internal systems, including Slack, offline while it investigates the breach. The alleged breach had reportedly forced Uber to take several internal communications and engineering systems offline.
The hacker’s screenshots appear to indicate full access to many critical Uber IT systems, including the company’s security software and Windows domain. The hacker also gained access to the company’s Amazon Web Services console, VMware ESXi virtual machines, Google Workspace email admin dashboard, and Slack server, to which the hacker posted messages.
How this attack worked initially (According to news and Twitter):
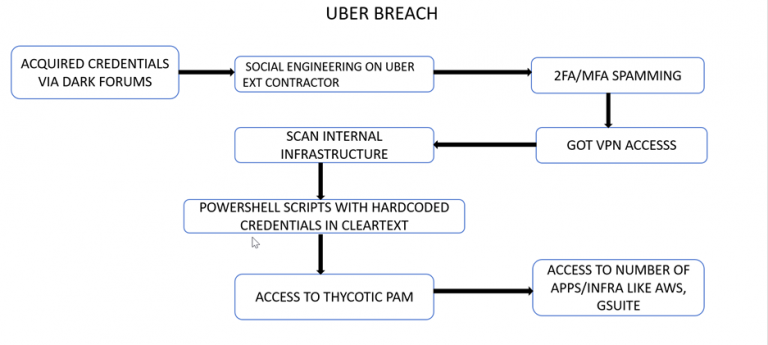
Investigation:
Uber has obviously taken notice of this, and they are currently looking into the issue.
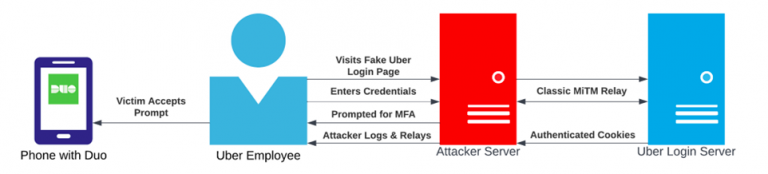
https://www.nytimes.com/2022/09/15/technology/uber-hacking-breach.htmlHow the attacker bypassed the MFA?:
For their employees, Uber appears to use push notification MFA (Duo). How might an attacker circumvent MFA?
Push, touch, and mobile MFA are frequently erroneously thought to protect users against social engineering. MiTM attacks typically continue to be a threat even when MFA can stop an attacker who merely has access to the victim’s credentials.
With the use of tools like Evilginx, an attacker can set up a counterfeit domain that delivers the legitimate Uber login page to the victim (an Uber employee). The question is how the attacker will persuade the victim to visit his phishing website.
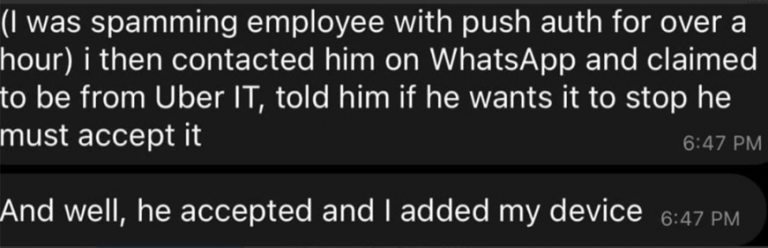
It was actually quite simple, the attacker continually pushed and denied the victim’s MFA requests to overwhelm him, and then he pretended to be an “IT” team over WhatsApp to convince the victim to visit his created phishing page and enter credentials on the totally fake Uber login page. The attacker obtains the logs and sends the response to his own local server.
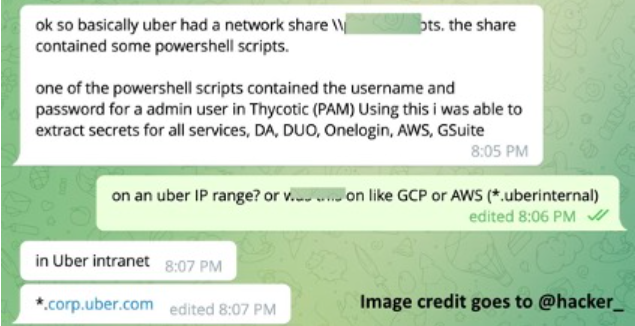
It appears that PowerShell scripts were located on a private network share. Using the admin user’s username and password from one of the Powershell scripts, the user was able to extract the secrets for all the services, including AWS, Gsuite, and others.
Once the attacker compromised an employee, they appear to pivot the internal network using the victim’s already-existing VPN connection.:
In this incident, it appears that the attacker discovered an internal network share that held scripts with privileged access, granting them the authority to control. Hackers allege that they have infiltrated the Duo, OneLogin, AWS, and GSuite infrastructures of Uber.
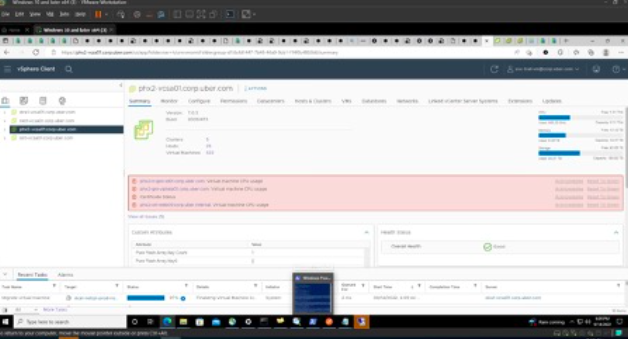
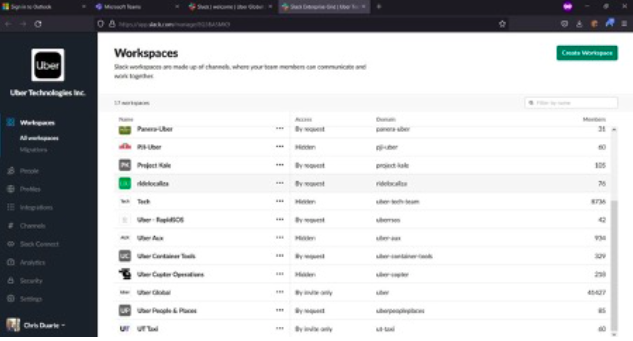
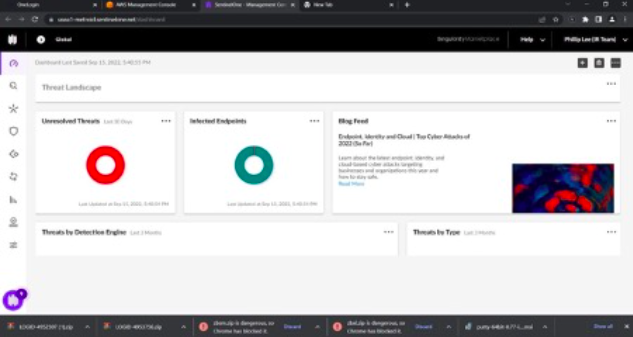
By tricking the victims into accepting a prompt that allowed the attacker to register their own device for MFA, the attacker claims they were able to secure persistent MFA access to their compromised accounts. Below are the screenshots from the Hacker:
Screenshot of Access to the database of administrator login data amassed by the threat actor behind the Uber attack. It is evident that he gained access to Uber’s internal network through a social engineering scam because those passwords seem to be secure.

The attacker shared several screenshots of Uber’s internal environment, including their Drive VCenter, sales metrics, Slack and even their EDR portal. Right now, the compromised HACKERONE account is the greatest concern for UBER. The attacker has access to all the vulnerabilities that were reported to UBER by different security researchers and given that the average SLA to apply a patch for a vulnerability ranges from one month to even six months, this is a serious concern.


As a preventative measure against these cyberattacks:
Conclusion:
The SecOps Group is a globally recognized IT security company having vast experience of providing cyber security consultancy and education services. Our core business comprises two units, consultancy and education. The SecOps Group offer CREST accredited security consultancy services and through our exams, we provide an authentic and credible certification program that is up-to-date and represents real life business risks.
Latest resources sent to your inbox weekly

Copyright © 2025 The SecOps Group. All Rights Reserved.